I was brought up to tell the truth. In fact, in the spirit of honesty, lying to me is about the most offensive thing someone can do to me. In business, it is one of those red lines that will kill a relationship immediately. Honour is wider than just honesty, it is also about living your values which widens the scope further. I passionately believe a business should be honourable.
We’ve blogged before about the level of lies which permeate this industry but have always confined our ire to the retail level of things – the bottom-feeders amongst them, often reselling BT’s IP service because it assists them in avoiding porting, who we call “scrotes”. They lie about their non-existent network, they reportedly lie about what their 7 year finance contracts are really for, they lie about their abuse of the porting process to optimise costs or extinguish suppliers.
However, in recent years, we’ve seen this spread to those who you would (or should) consider above it. I’m talking about one-time FTSE-100 listed companies and carriers who should be firmly under Ofcom’s gaze. I can think of two examples, at this much less-populous end of the industry, where in my opinion and belief based on 30-odd years of experience, they have outright lied. I don’t have inside knowledge to know or prove this, but I think I’d qualify as an expert witness and would happily share my views and reasons for doubt under oath. I believe they’ve done so to avoid owning up to bad news, to hide the truth and ultimately to mislead current and future customers over what went on, presumably hoping to sweep it under the carpet and get back to curating an image of virtue and competence.
Let me be very clear: I’m not celebrating other operators having outages, however caused. No doubt, competence is a variable affecting how many and how often, but the real issue here is the extent to which they are disclosed and owned by those concerned. We all have issues and if you look back through https://status.simwood.com you’ll find some of ours, going back 10 years. It is inglorious but it accurately reflects history, and moreover, the history it reflects we owned. You’ll also find blogs about issues we had that you never heard about until we felt obliged to flog ourselves in public. So this isn’t a celebration, nor is it a ‘look at us’ post. I’m simply saying: be less shit, and be honourable.
Colt had a cyber-attack in August which is still severely impairing their services. We don’t care too much now they’re porting at least some numbers again, although publicly they never admitted they weren’t and that they still aren’t fully. We knew about the attack from cyber-security circles a few days before they admitted anything and their conduct since has, in my opinion, been to downplay and mislead. Their oh-so-transparent status page at https://www.colt.net/status/ hasn’t been updated in a few months because they resorted to emailing instead, and the incident page they put up in the interests of “transparency” (https://www.colt.net/go/cyber-incident/ ) has HTML headers preventing indexing by search engines:
<meta name='robots' content='noindex, follow' />Meanwhile the scope of the incident – a compromise of a Sharepoint server which hadn’t been patched for a vulnerability – seems severely downplayed. We’ve heard all sorts of tales around the industry from them losing their European vmWare cluster, to staff having no laptops, to sales reps mailing customers from Hotmail and Gmail. Of course, we don’t know if any of that is remotely true, and certainly there will be conjecture and rumour in there, but it doesn’t take nearly 3 months to recover from a compromised server containing only old CVs and porting data. They assure customers no data was lost yet it was for auction on-line and clearly in the possession of the hackers – we know as there were Simwood-related documents in there in the auction listing which we authenticated.
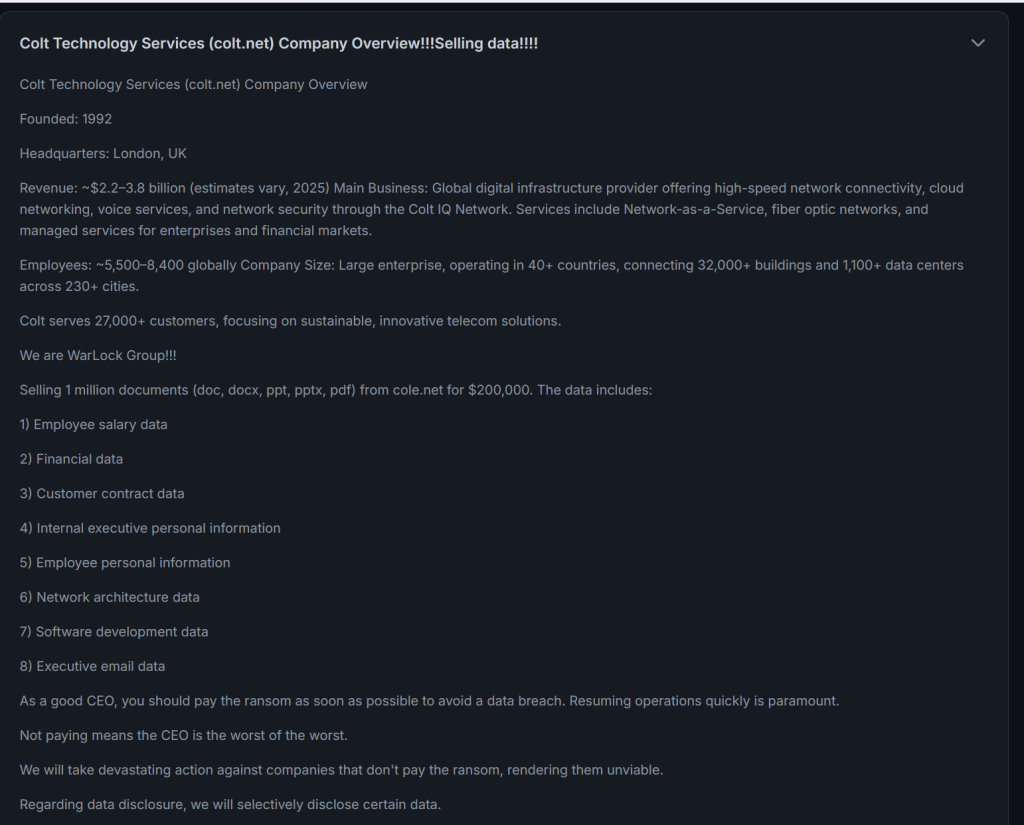
To top it all off, an ill-advised article in Capacity magazine quotes the CEO saying “Almost every conversation that we had with our customers and suppliers started with them saying: If it wasn’t you, it would be us”. Really? Whilst the threat is pervasive and everyone has a weak-point, this passes off what happened, and moreover what they’ve done since, as just being one of those things, like a stolen pen from reception. This is a Tier 1 operator as far as the allegedly stringent security regulations are concerned. We hope Ofcom and the various other agencies involved with this will be asking searching questions and exposing some answers.
At the opposite end of the scale we have Magrathea. We wouldn’t normally name them but frankly I’ve had enough of their pious bullshit. Their “status page” has always been a joke, looking statically maintained with zero history. We are limiting quotes in this blog to what has been put out in the public domain (which is little), but suffice to say Magrathea’s post-incident reports are comical. They range from absolutely no insight into the root cause of the issue, to codifying a complete lack of awareness of the most basic tenets of the prevailing security legislation.
As entertaining as they are, last week’s issue was the final straw, seemingly blaming AWS because it was en vogue to do so, despite AWS having already fixed the esoteric DNS issue that exposed those with poorly designed DynamoDB deployments.
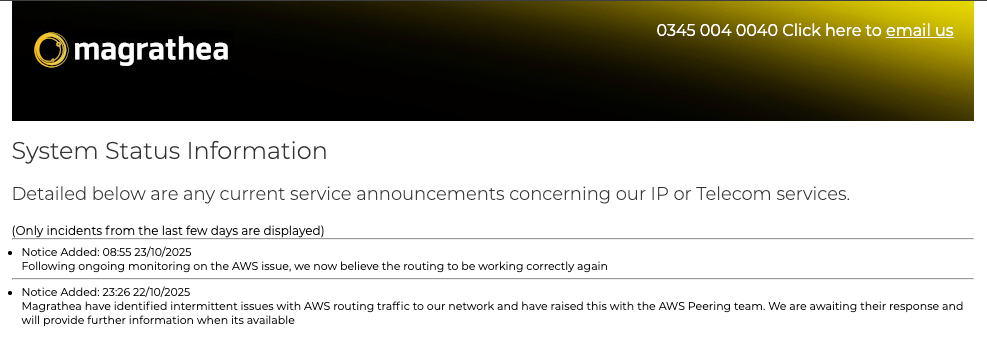
We’ve made FOI requests on Ofcom to enquire which of their many outages that appear to require an incident report to be filed, have had one filed. The answer: none.
I can’t think of any other industry, let alone regulated industry where this kind of nonsense would be tolerated and operators wouldn’t either be shut down by the consumer guardians, or run out of town by their customers. Something is very wrong that this is tolerated by both and these kinds of operators are allowed to exist.
It is even award winning apparently but that is a whole other rant for another day!
As an industry, we have to do better.

